
System i Software
Next Step
Product Information
- iSecurity Overview
- iSecurity Action
- iSecurity Anti-Virus
- iSecurity AP-Journal
- PTF Tracker
- iSecurity Assessment
- iSecurity Audit
- iSecurity Authority on Demand
- iSecurity Capture
- iSecurity Central Administration
- iSecurity Command
- iSecurity Compliance Evaluator
- iSecurity Firewall
- iSecurity GUI
- iSecurity Native Object Security
- iSecurity Password
- Password Reset
- iSecurity Screen
- iSecurity Safe Update
- iSecurity System Control
- iSecurity User & System Value Replication
- iSecurity View
- iSecurity Visualizer for Audit
- iSecurity Visualizer for Firewall
- AP Journal
- Change Tracker
- DB Gate
- Filescope
- i4XML
- LinkIt
- View
- Window Menu
- VTLBackup4i
View
Overview
View provides top-notch field-level security by restricting access to specific fields and records in System i (AS/400) databases.
View ensures state-of-the-art, field-level security that restricts access to specific fields and records in System i databases without recompiling existing user programs. This innovative, patent-pending solution guarantees bulletproof control of your company's private information.
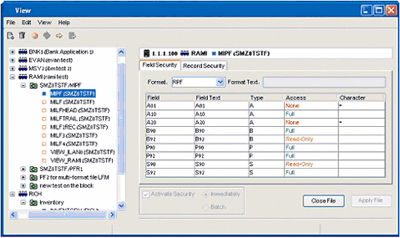
View Java GUI
View: The Only One of its Kind
OS/400 security and other third-party solutions provide protection at the object level only. But View is unique. It lets systems administrators create rules that define which users are authorized to view or modify the contents of individual fields in a database. If a user does not possess the proper credentials, he cannot see or modify the data in a protected field, but can continue to work with data in unprotected fields.
View is User-Friendly
The smooth, non-technical interface and quick, concise movement between tasks keep user time down to a minimum. View lets you set your parameters and get back to work, with no time wasted.
View Puts You in Control
Why worry about prying eyes? Unauthorized access to sensitive data has serious ramifications, including identity theft, stolen credit records, or email address harvesting. But not with View! With View+++, you control WHO sees WHAT and WHEN.
Key Features and Benefits
- Allows administrators to restrict fields and records to selected, specific users
- Quick, easy modification of user and user-group profiles
- Defining file and field restrictions is a snap
- User-friendly, intuitive, GUI
- Designed for ease of use by non-technical personnel
- Color-coded file navigation system
- Lightning fast operation - does not waste precious system resources
- Minimal disk space requirements
Financial Institutions
- Prevent unauthorized entry or modification of financial transactions
- Ensure client confidentiality
- Ensure compliance with regulations governing financial activity
Health Care Providers
- Guarantee patient privacy
- Ensure compliance with data security and privacy regulations
e-Business
- Ensure client transaction security
- Prevent identity theft and e-mail address harvesting
Industry and Commerce
- Maintain security of confidential data
- Comply with newly enacted regulations for corporate governance
The software is available for a FREE Proof of Concept evaluation, for more details email [email protected] or call +61-3 9572-5869



